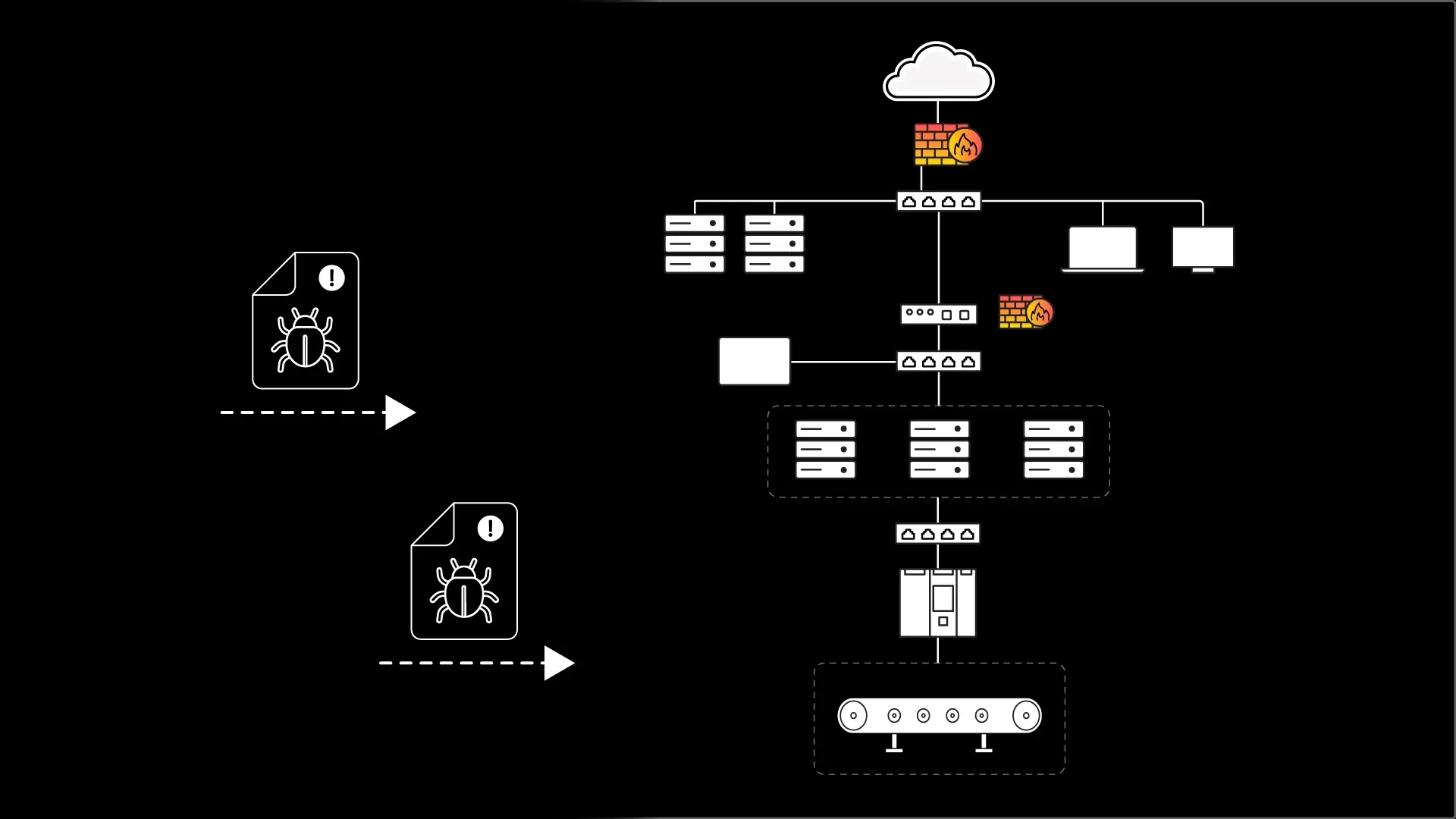
It is often said, “The Internet is a bad neighborhood”. And as true as that seems to be, there are many other risks and threats that automation engineers need to be aware of that can affect computer systems used in automation and control.
Operational technology, or OT, refers to the physical hardware and software used to monitor and control industrial equipment, processes, and infrastructure. These are the items we as automation engineers work with every day.
This article will take a hard look at the risk factors in OT cybersecurity and how you can reduce these risks.
Critical infrastructure, such as energy plants, dams, and wind farms, as well as critical manufacturing plants, needs to be aware of the many threats that their systems face. For instance, threats can come from a disgruntled employee who knowingly infects the network with a virus.
Threats can come from an external source, such as the internet. Each of these threat types could do significant harm to the plant’s OT infrastructure.
What risks do your systems need to guard against? Just doing what others do or haphazardly employing cybersecurity hardware and software isn’t enough to ensure safety.
A systematic approach to cybersecurity is a required vital step in eliminating risks and making your systems a more friendly neighborhood.
Fundamentals of OT cybersecurity risk assessment
OT risk assessment is defined as the systematic process for identifying, evaluating, and prioritizing threats and vulnerabilities. There are several characteristics unique to OT environments that differ from IT environments.
Among these are the prevalence of legacy systems, 24/7 availability requirements, and physical integrations to machines, actuators, and sensors that make up the manufacturing process.
Risk assessments must involve all affected stakeholders, including operations, engineering, IT, and management personnel. As I mentioned previously, this assessment of risk must follow a systematic approach for it to be successful.
So, let’s take a look at the five steps involved in this assessment.
Asset identification and inventory
When an insurance company is asked to insure your home, they want to know what is in the home so that they know what may be lost, or in other words, what is at risk of loss or damage. The same holds true with risk assessments in cybersecurity.
Inventorying and mapping of all of your OT assets is the first critical step. Everything should be listed in the inventory, including hardware such as PLCs, SCADA systems, and HMI stations. This inventory must include all software and firmware installed on your OT systems.
These assets may not appear to be physical in nature, but they are at risk and the easiest assets for hackers to infect.
We must also include network equipment such as switches and cabling. And don’t forget external connections such as data ports provided for vendor access or connections for remote maintenance.
A complete inventory is crucial to allow the risk assessment team to fully understand what is called the “threat landscape”.
Missed items, such as data ports provided for vendor access, can be easy routes for system infection, even if not maliciously done.
Threat and vulnerability identification
Once we have all of our assets listed, we know all of the items that might be attacked. Next, we need to identify the types of threats our systems may invite.
These threats can be internal threats from insiders, such as skimming funds from accounts or inadvertent misconfigurations of network switches that allow bypassing of user authentication requirements.
The threats can also be external from internet sources, malware, hackers, or nation-state actors after valuable assets, such as formulations and recipes.
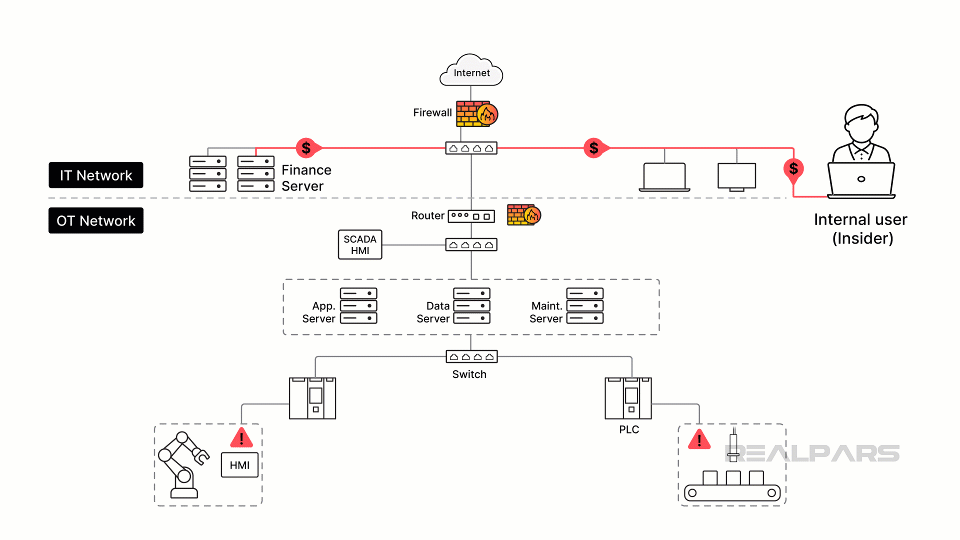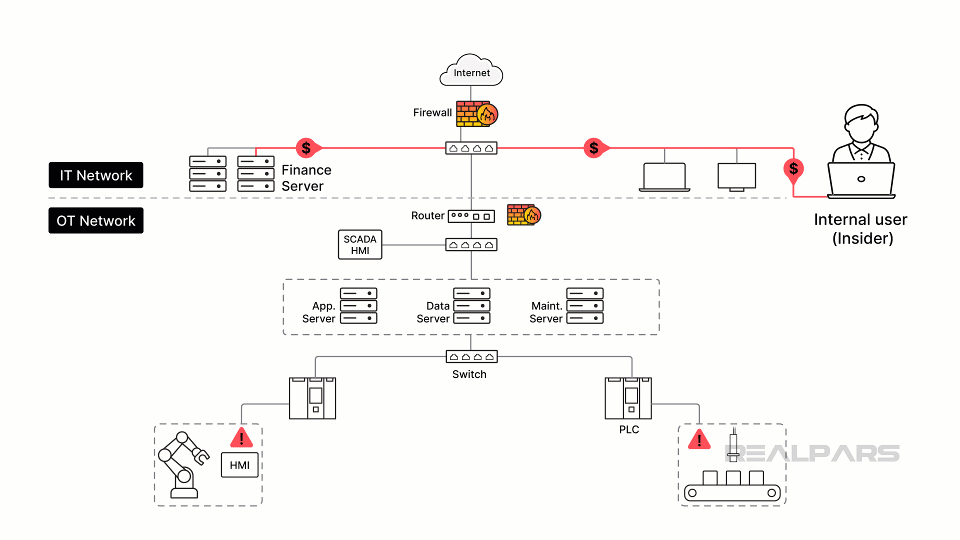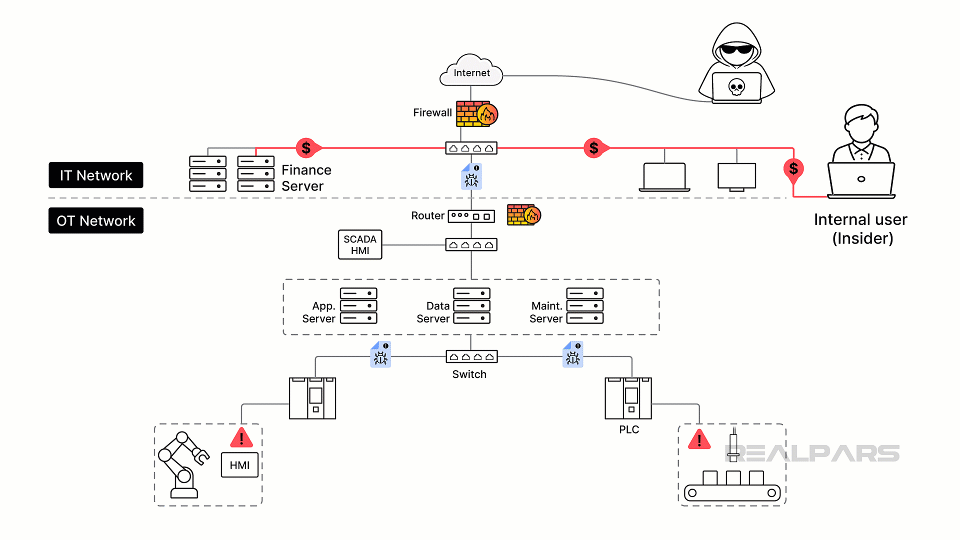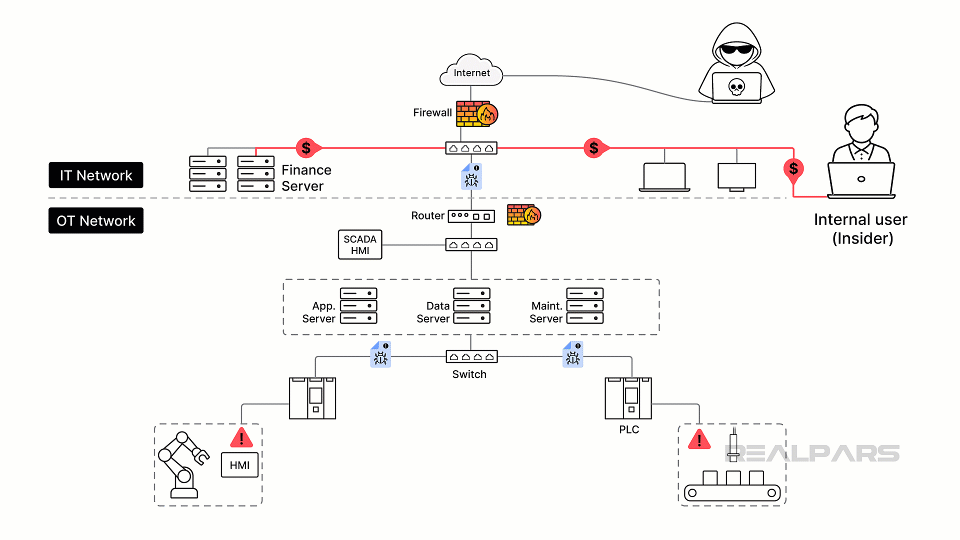
Often forgotten are common vulnerabilities that can occur with legacy OT hardware and software, such as the lack of patching, weak authentication, and insecure protocols.
Impact analysis
Now that we know our threat landscape, we must assess the consequences of actually having a compromised system due to an attack.
These consequences can take many forms, such as safety risks to personnel or the environment, disruption to production, operational disruptions, financial losses, reputational damage, and regulatory and compliance violations.
The consequences your facility may face depend on your unique situation and may include many other risks.
Likelihood assessment
The next step is the hardest — determining the likelihood that these consequences will actually be realized.
Determining the probability of exploitation of your system’s vulnerabilities involves predicting your exposure to internet threats, identifying known exploits and adversary capabilities, and, importantly, the history of incidents that have affected systems like yours.
For example, Stuxnet was a pervasive and debilitating virus that attacked the hardware of a specific supplier. The Colonial Pipeline attack was a ransomware cyberattack that led to a shutdown of operations and significant fuel shortages across the East Coast. What can happen to your operation, and how likely is it to happen?
The Risk Matrix
The final step is to construct a Risk Matrix for each risk factor. The Risk Matrix typically lists the impact of a cybersecurity breach against the likelihood that the breach will occur. Here is an example matrix using thresholds for impact and likelihood as low, medium, and high.
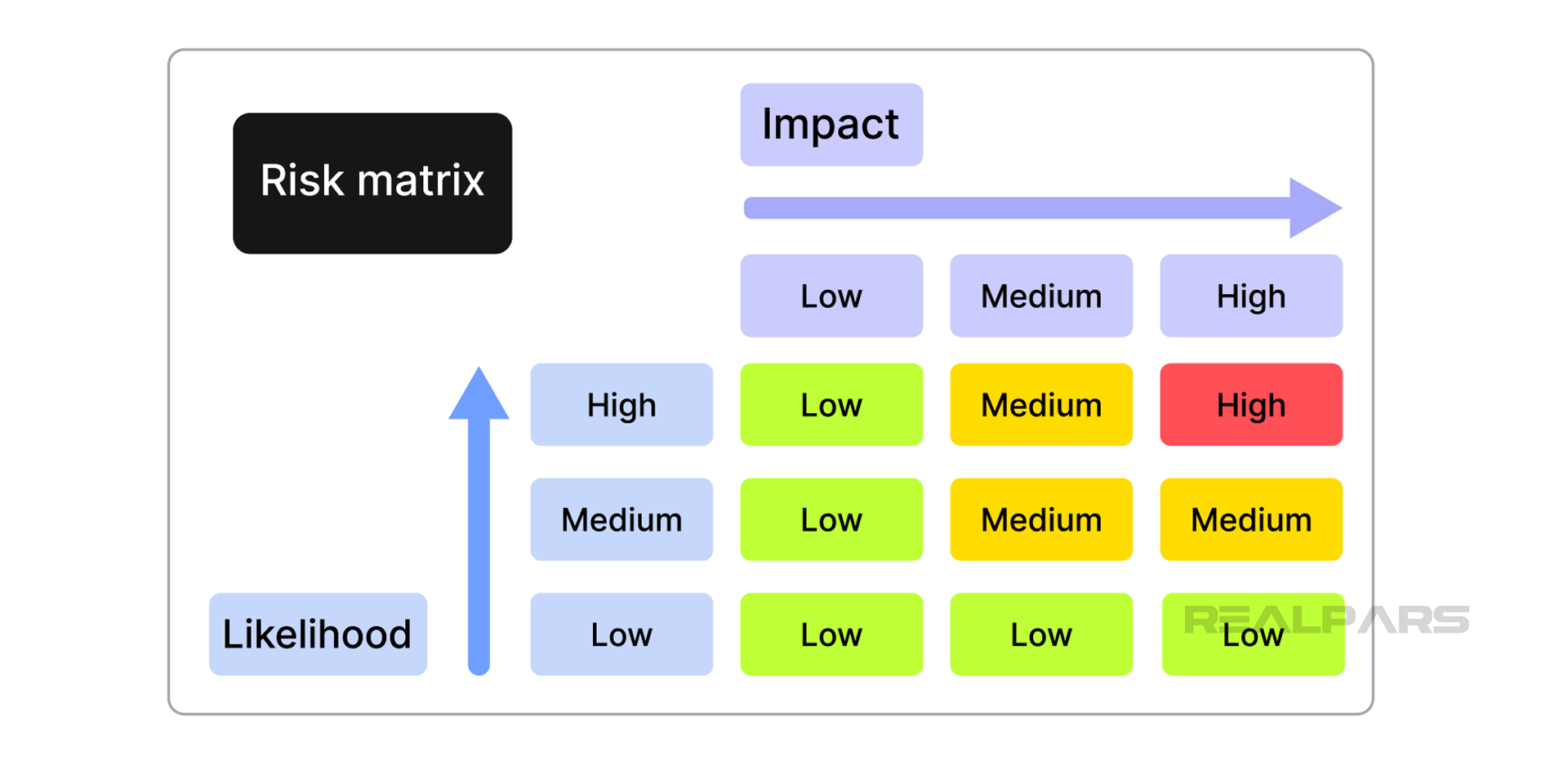
The risk assessment team is responsible for determining the best allocation of risk to each square on the matrix. Your team may determine that a high probability of occurrence with a medium impact would also qualify as a high risk. The rankings depend solely upon your unique situation.
Why generate this matrix? It allows you to easily identify risks that require immediate mitigation, such as all high-risk items, as well as those that can be deferred, such as those with a low risk.
Companies have limited budgets for cybersecurity, so the highest-risk issues should be addressed first.
Challenges and considerations in OT risk assessment
This process is not usually an easy one. Items such as understanding all of the constraints to patching legacy systems can be difficult. There may be limited visibility as to the nature of some threats.
There may be organizational barriers to obtaining all of the data required to assess the breadth of some threats. There may be supply chain and third-party risks that are unknown.
Best practices for effective OT risk assessment
There are best practices for overcoming some of these constraints and developing an effective risk profile. The most important is for all stakeholders to be involved and collaborate in the assessment.
To aid in this process, there are many standards and frameworks available that guide teams in the risk assessment process such as NIST CSF and IEC 62443.
A key to effective cybersecurity risk assessment programs is to periodically update the assessment using current data.
Conclusion
OT cybersecurity risk assessments are the foundation for creating an effective defense against internal and external threats. By engaging all stakeholders in the process, the most complete picture of the threats and likelihood of occurrence can be determined and plotted in a risk matrix.
From the risk matrix, the proper decisions can be made for employing cybersecurity defenses. As OT risks evolve, it is important for facilities to be proactive and conduct ongoing risk assessments as the foundation of their OT cybersecurity program.