What is OT network security?
Chances are, you have personally been affected by data breaches at your bank, credit card company, or social media account. These are all examples of breaches in cybersecurity.
If you’d prefer watching instead of reading, check out the video below. Otherwise, feel free to skip it and continue with the blog.
Just as cybersecurity breaches affect individuals, industrial operations, such as manufacturing, power generation, water treatment, and transportation, are also at risk of targeted attacks, which can lead to physical disruptions and financial loss.
That is why it is vitally important for automation engineers to understand the application of effective OT cybersecurity.
While OT cybersecurity covers a broad range of concerns, including physical access, system integrity, and secure development, the following content and associated course focus specifically on the network layer that forms the backbone of any industrial cybersecurity strategy.
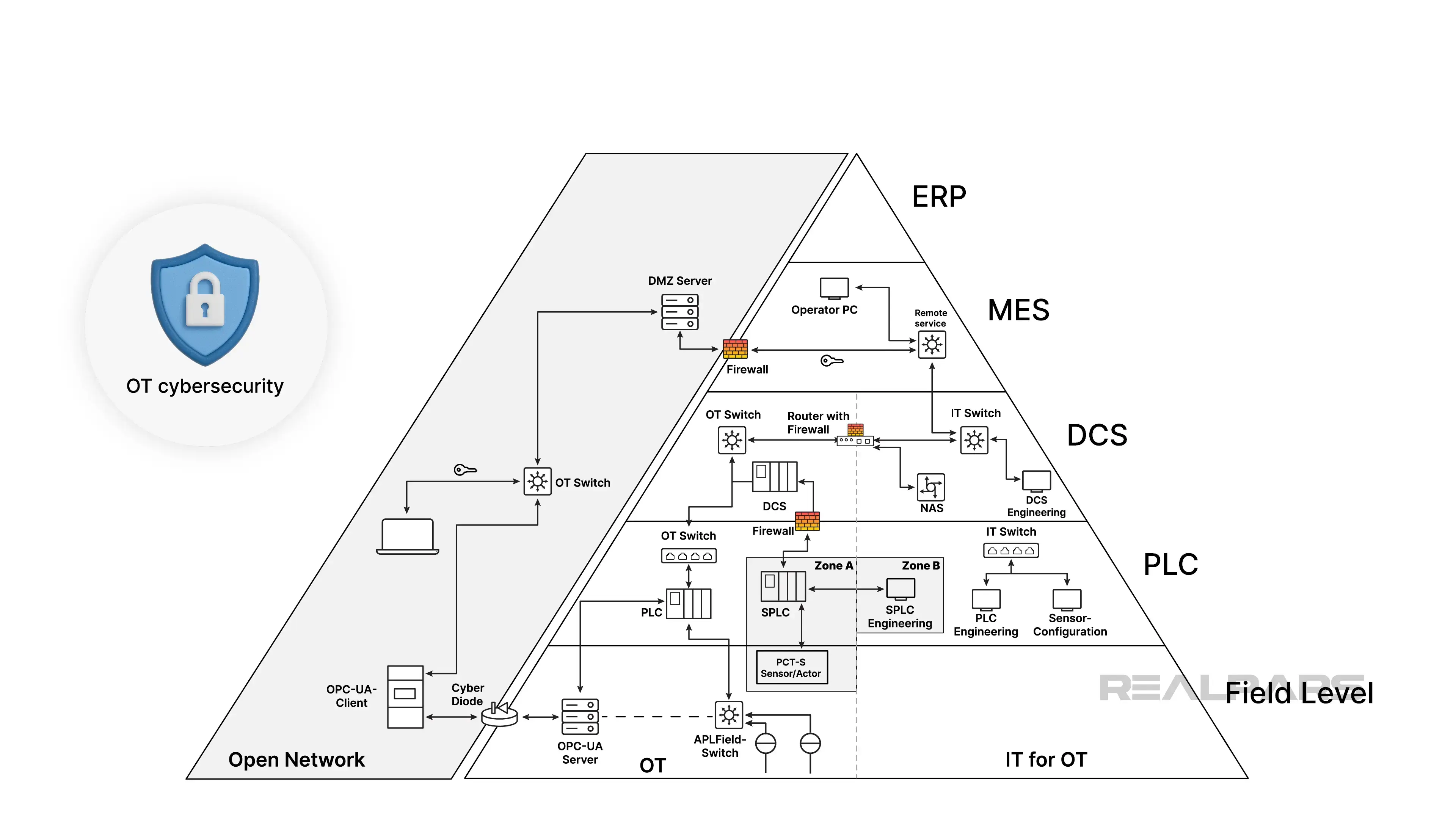
OT cybersecurity can be understood as the protection of industrial systems, including hardware, software, networks, and operational processes, from threats that could compromise safety, availability, integrity, or data confidentiality.
These threats can result in unauthorized information disclosure, theft, or damage to assets, as well as disruption or misdirection of the services they support.
The Importance of OT Cybersecurity
It is apparent we would not want hackers to steal our personal information, and the same goes for manufacturing operations.
Threat actors may seek to disrupt operations, steal intellectual property, or extort financial gain through methods like ransomware. In industrial environments, where availability and safety are top priorities, the impact of such breaches can be especially severe.
An example is the use of phishing emails to trick the user into clicking a link that installs a ransomware virus that locks up the user’s computer until a monetary payment is made.
Another motivation is simply to exploit weaknesses in the target’s computer system just to cause disruption in operations.
The foremost reason these attacks happen is improper OT network design and insufficient OT Cybersecurity defenses.
Companies need to be aware of all of the ways that hackers can penetrate computer systems: email, internet connections, USB ports, injection of malicious code, serial interface ports, just to name a few.
Stopping cyberattacks involves multiple steps and a coordinated plan that is well thought out, supported by management, and continually audited and improved.
Why threats are evolving over time
OT Cybersecurity threats have evolved over time, from simple theft of login credentials and email scams from lone hackers to multinational crime rings that have devised ways to penetrate OT networks without leaving a trace.
These modern hackers take advantage of the increasing digital footprint of our OT operations, including wireless tablet use to log data, robotic warehousing operations, and storage of confidential recipe and production data in large databases.
Even a simple breach of a database can lead to devastating consequences, including theft of intellectual property and financial data.
Preventing OT cybersecurity breaches
So how can industrial organizations stop these types of attacks?
The first step is adopting a structured cybersecurity framework, and IEC 62443 is among the most widely recognized. It guides organizations through a lifecycle approach: from identifying assets and risks, to segmenting networks into protected zones, and applying controls based on threat levels.
Leading network device providers, such as Moxa, are committed to providing reliable and secure networking devices and following a comprehensive approach to cybersecurity, including implementing rigorous security-by-design principles, continuous monitoring of vulnerabilities, and prompt incident response protocols to support customers in building resilient OT networks.

Next, perform a risk-based assessment. This includes identifying critical assets, evaluating vulnerabilities, and mapping potential attack paths. A thorough inventory of infrastructure, including hardware, software, interfaces, and vendor access, is essential to understanding risk exposure.
Then, design your system architecture using the zone-and-conduit model. This strategy separates the network into zones with similar security requirements (for e.g., PLCs, SCADA, (and) servers) and defines secure communication paths (conduits) between them.
Appropriate protections, such as firewalls, authenticated switches, and routing policies, are applied at zone boundaries.
Your network devices matter. Switches, routers, and intrusion detection systems should be selected carefully. Products developed under a Secure Development Lifecycle (or SDL), as defined in IEC 62443-4-1, follow rigorous security practices like threat modeling, secure coding, vulnerability tracking, and patching support.
Many leading vendors, including Moxa, have achieved SDL certification. While this doesn’t eliminate all risks, it provides assurance that security was embedded from day one, not added as an afterthought.
Common security features include user authentication, SSL/SSH encryption, VLAN segmentation, and centralized access controls.
Lastly, continuous monitoring and improvement are essential. Implementing traffic monitoring, anomaly detection, and regular auditing allows early detection of potential breaches and ensures ongoing alignment with security objectives.
Keeping up with the bad guys
OT Cybersecurity intruders are everywhere and are constantly looking for vulnerabilities in OT networks that they can exploit. Some of these actors are out to simply cause disruption, but many have very bad intentions.
As the nature of OT Cybersecurity threats grows, your OT networks should be evaluated and upgraded as well to meet these new threat challenges.
Remember, steps to a secure network include:
- Perform a risk assessment to identify assets and vulnerabilities
- Plan your OT network around a proven reference architecture
- Use SDL-certified switches, routers, and security appliances that reference industrial cybersecurity standards and are built based on a certified secure development life-cycle to protect your network
- (and) Develop procedures for monitoring, auditing, and continuous improvement in your OT Cybersecurity strategy.
Join hundreds of plant managers who trust RealPars to train their teams! Visit realpars.com/business and let us help you take your team's skills to the next level. The link is in the description below!

.jpg)